Top Tips for Ensuring Secure Data Destruction in Your Cyber Security Plan
Top Tips for Ensuring Secure Data Destruction in Your Cyber Security Plan
Blog Article
Just How Appropriate Information Destruction Adds To Robust Computer System Safety And Security Providers and Mitigates Threats of Data Breaches
In today's electronic landscape, the relevance of correct information damage can not be overemphasized, as it functions as a fundamental component of thorough computer system safety services. By applying effective information erasure techniques, organizations not just shield sensitive information from unauthorized accessibility however also strengthen their conformity with regulative frameworks - data destruction. The ramifications of insufficient data destruction prolong beyond plain conformity; they can greatly impact an organization's cybersecurity position and track record. Recognizing these dimensions elevates essential questions regarding the methods in location and their effectiveness in an era of escalating cyber dangers.
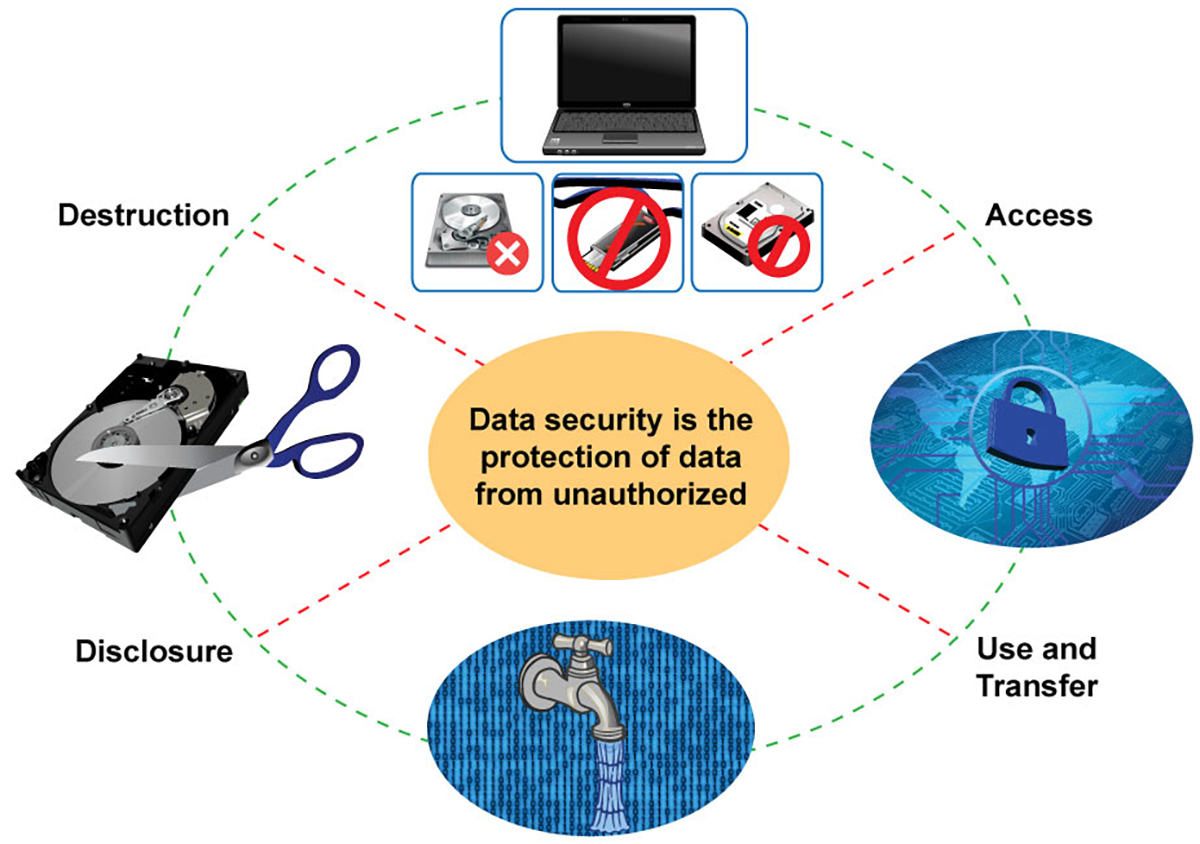
Value of Data Damage
In today's digital landscape, the value of information destruction can not be overstated. As organizations progressively depend on electronic properties, the possible threats related to data violations and unauthorized gain access to magnify. Reliable information destruction is a vital part of an extensive information protection method, guarding delicate details from coming under the hands of malicious actors.
When information is no more required, just removing data or formatting tough drives wants. Residual information can commonly be recuperated using readily offered devices, presenting substantial dangers to both companies and people. This underscores the requirement for durable information damage practices that make certain all information is irretrievably gotten rid of.
Additionally, governing conformity mandates, such as GDPR and HIPAA, stress the commitment to secure delicate data, including its correct disposal. Non-compliance can bring about serious financial charges and lawful consequences. data destruction. Thus, incorporating effective information devastation protocols not just improves safety and security yet likewise strengthens a company's credibility and reliability

Techniques of Secure Information Erasure
A number of effective techniques of safe information erasure can be employed to make certain that sensitive details is completely eliminated from storage space devices. One extensively acknowledged method is information overwriting, which involves replacing existing information with random patterns several times. This approach substantially decreases the opportunities of information recuperation, although it might not work against sophisticated forensic strategies.
Physical damage is likewise a reliable technique, where storage space devices are rendered pointless via shredding, crushing, or incineration. This technique ensures that data can not be recuperated by any type of ways yet calls for mindful handling of hazardous materials.
Lastly, specialized software application devices made for safe and secure information erasure provide capabilities that adhere to various erasure standards. These tools frequently include features like verification procedures to confirm effective information devastation.
Using these techniques in mix can enhance data protection and reduce the risks associated with data breaches, guaranteeing that delicate info is not inadvertently exposed.
Legal and Conformity Considerations
The approaches employed for safe data erasure not only serve to protect delicate info yet likewise has to line up with legal and conformity frameworks controling data protection. Organizations are called for to comply with various policies, such as the General Information Defense Guideline (GDPR), the Medical Insurance Mobility and Liability Act (HIPAA), and the Payment Card Sector Information Safety Criterion (PCI DSS) These policies mandate details protocols for information taking care look these up of and destruction, making sure that delicate and individual information is irretrievably removed when no longer required.
Failure to adhere to these lawful needs can cause substantial charges, consisting of penalties and reputational damage. In addition, companies should preserve records of data destruction processes, showing compliance during audits or examinations. This documentation not just shields against legal effects yet likewise strengthens trust with stakeholders and clients, showcasing a commitment to information security.
Incorporating lawful and compliance factors to consider right into information destruction methods is important for any type of organization. It decreases the threat of information violations and shows a positive method to protecting sensitive information, ultimately promoting a culture of safety and responsibility across the organization.
Effect On Cybersecurity Pose
Efficient information devastation dramatically boosts a company's cybersecurity posture by minimizing the possible attack surface area for cyber risks. When delicate data is not correctly damaged, it remains obtainable to harmful stars who can manipulate this details for unauthorized accessibility, identification theft, or corporate espionage. By implementing robust data damage methods, companies can properly decrease the risk of data breaches and boost their total safety and security structure.
Moreover, the secure disposal of unnecessary or obsolete information not just safeguards delicate information yet likewise helps organizations abide by industry laws and requirements. Failing to sufficiently destroy data can lead to extreme lawful effects and reputational damage, more jeopardizing an organization's cybersecurity stance.

Ultimately, focusing on efficient data destruction is necessary for cultivating a durable cybersecurity pose, ensuring that organizations remain alert against progressing cyber dangers while protecting their crucial possessions and stakeholders.
Best Practices for Organizations
Executing finest techniques for information devastation is crucial for companies intending to secure delicate details and minimize cybersecurity threats. Companies must establish a comprehensive information damage policy that details duties and treatments. This policy needs to follow relevant guidelines, such as GDPR or HIPAA, ensuring lawful conformity.
Secondly, it is important to utilize approved information sanitization methods, consisting of data cleaning, degaussing, and physical devastation, tailored to the kind of information and storage space medium. Employing qualified experts for information damage solutions improves the reliability of these approaches.
Additionally, organizations need to maintain a comprehensive inventory of all data storage space gadgets, making certain that all obsolete or changed devices undertakes damage. Regular audits of data damage practices can help determine weak points and improve conformity.
Employee training is an additional vital facet, as staff should comprehend the importance of information devastation and stick to established methods. Companies should record all information damage activities to provide liability and traceability, which can be very useful throughout audits or in the occasion of you can find out more a violation.
Conclusion
One extensively acknowledged approach is data overwriting, which includes changing existing information with random patterns several times.The approaches utilized for secure data erasure not just offer to protect sensitive info yet also should straighten with lawful and conformity structures governing data security. These laws mandate particular procedures for information dealing with and devastation, ensuring that delicate and individual data is irretrievably erased when no longer required.
By executing durable information devastation protocols, companies can efficiently reduce the danger of information violations and boost their total safety structure.
In verdict, proper data destruction is essential for improving computer system security services and reducing the dangers associated with information violations. - data destruction
Report this page